7. Troubleshooting¶
7.1. Diagnostic Mode¶
If module doesn’t work as you expect, it’s worth to enable “Diagnostic Mode”.
This will output logs that describes how the module is working.
They can also diagnose issues that can occur like: config errors, failed login process, etc.
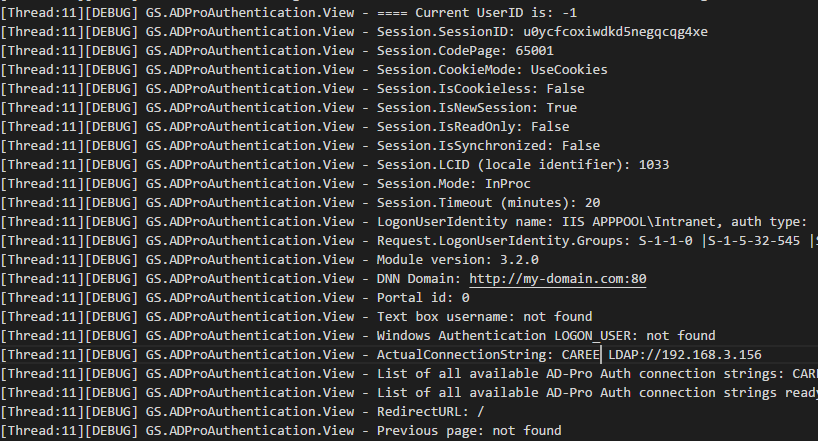
Logs are created in file that is located in ~\Portals\_default\LogsYYYY.MM.DD.logs.resources, see log example below:
Logs are created only when plugin is working in “Diagnostic Mode”, to enable it please follow steps below:
Open log4net configuration file
DotNetNuke.log4net.config, it can be found in DNN root folder, see figure below: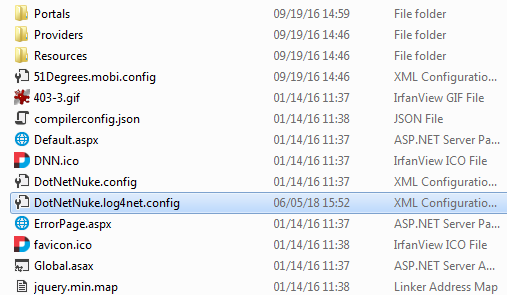
Inside that file set log level to
ALL, see code snippet below:<root> <level value="ALL" /> <appender-ref ref="RollingFile" /> </root>
Go to provider settings, these steps are described in chapter Accessing settings panel.
Select
Other Settingstab, and enable optionDiagnostic Mode, see figure below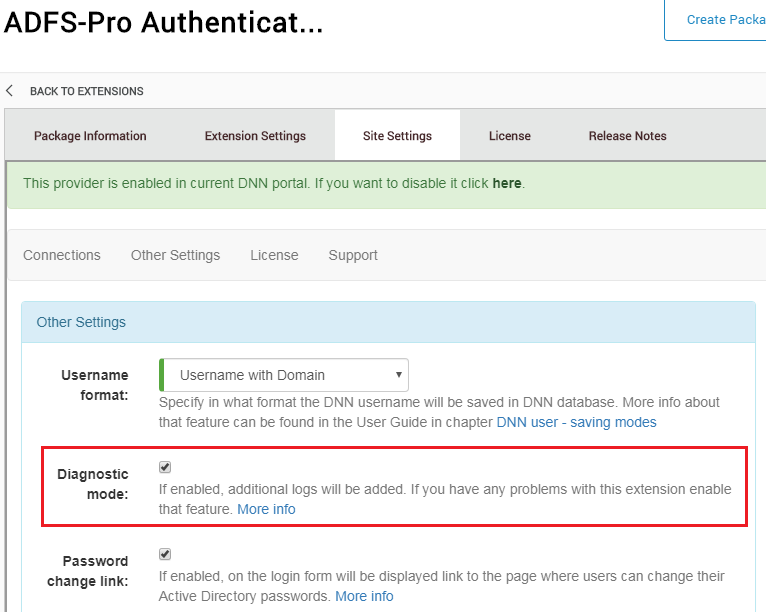
Logging mechanism is turned on, reproduce the sign-in process and check the log file.
7.2. JavaScript issues¶
7.2.1. Overview¶
User interface is created at the top of AngularJS framework. JavaScript can be moody although it’s very fast. If you will see interface issues, for example view can’t be loaded or displayed, buttons aren’t responding, it’s worth to check JavaScript errors. Depending what browser you are using, check following articles that are describing how to display these errors in your browser:
If you have any problems with your plugin, please send above error messages to support@glanton.com
7.2.2. Edit & Delete buttons doesn’t work¶
When you can’t update module settings, and JavaScript throws error like Method Not Allowed... or requests throws 405 HTTP error code, please make sure that WebDAV is disabled.
To disable WebDAV, please add following lines to the web.config file, in the section system.webServer-> modules add following line:
<modules>
<remove name="WebDAVModule"/> <!-- add this -->
...
</modules>
in the section system.webServer-> handlers add following line:
<handlers>
<remove name="WebDAV" />
...
</handlers>
the ExtensionlessUrl-Integrated-4.0 handler under the system.webServer-> handlers also applies the verb PUT:
<handlers>
...
<remove name="ExtensionlessUrl-Integrated-4.0" />
<add name="ExtensionlessUrl-Integrated-4.0" path="*." verb="GET,HEAD,POST,DEBUG,PUT,DELETE" type="System.Web.Handlers.TransferRequestHandler" preCondition="integratedMode,runtimeVersionv4.0" />
...
</handlers>
Here you can read more about WebDAV.
If this will not help add following code snippet to the web.config:
<modules runAllManagedModulesForAllRequests="true">
<!--IISFIX: Whatever this is, it causes 405 Method Not Allowed errors on IIS when using PUT. (Microsoft's broken by defult)-->
<remove name="WebDAVModule"/>
</modules>
<handlers>
<!--IISFIX: ASP.net is broken by default. By default they will not accept verbs from the client.
First we have to rip out everything related to ASP.net-->
<remove name="ExtensionlessUrlHandler-ISAPI-4.0_64bit"/>
<remove name="ExtensionlessUrlHandler-Integrated-4.0"/>
<remove name="ExtensionlessUrlHandler-ISAPI-4.0_32bit"/>
<remove name="SimpleHandlerFactory-ISAPI-2.0-64"/>
<remove name="SimpleHandlerFactory-ISAPI-2.0"/>
<remove name="SimpleHandlerFactory-Integrated"/>
<remove name="SimpleHandlerFactory-Integrated-4.0"/>
<remove name="SimpleHandlerFactory-ISAPI-4.0_64bit"/>
<remove name="SimpleHandlerFactory-ISAPI-4.0_32bit"/>
<!-- IISFIX: Now that we're ripped out everything related to ASP.net, put them back correctly.-->
<add name="SimpleHandlerFactory-ISAPI-4.0_32bit" path="*.ashx" verb="*" modules="IsapiModule" scriptProcessor="C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_isapi.dll" resourceType="Unspecified" requireAccess="Script" preCondition="classicMode,runtimeVersionv4.0,bitness32" responseBufferLimit="0"/>
<add name="SimpleHandlerFactory-ISAPI-4.0_64bit" path="*.ashx" verb="*" modules="IsapiModule" scriptProcessor="C:\Windows\Microsoft.NET\Framework64\v4.0.30319\aspnet_isapi.dll" resourceType="Unspecified" requireAccess="Script" preCondition="classicMode,runtimeVersionv4.0,bitness64" responseBufferLimit="0"/>
<add name="SimpleHandlerFactory-Integrated-4.0" path="*.ashx" verb="*" type="System.Web.UI.SimpleHandlerFactory" resourceType="Unspecified" requireAccess="Script" preCondition="integratedMode,runtimeVersionv4.0"/>
<add name="SimpleHandlerFactory-Integrated" path="*.ashx" verb="*" type="System.Web.UI.SimpleHandlerFactory" resourceType="Unspecified" requireAccess="Script" preCondition="integratedMode"/>
<add name="SimpleHandlerFactory-ISAPI-2.0" path="*.ashx" verb="*" modules="IsapiModule" scriptProcessor="%windir%\Microsoft.NET\Framework\v2.0.50727\aspnet_isapi.dll" resourceType="Unspecified" requireAccess="Script" preCondition="classicMode,runtimeVersionv2.0,bitness32" responseBufferLimit="0"/>
<add name="SimpleHandlerFactory-ISAPI-2.0-64" path="*.ashx" verb="*" modules="IsapiModule" scriptProcessor="%windir%\Microsoft.NET\Framework64\v2.0.50727\aspnet_isapi.dll" resourceType="Unspecified" requireAccess="Script" preCondition="classicMode,runtimeVersionv2.0,bitness64" responseBufferLimit="0"/>
<add name="ExtensionlessUrlHandler-ISAPI-4.0_32bit" path="*." verb="*" modules="IsapiModule" scriptProcessor="C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_isapi.dll" resourceType="Unspecified" requireAccess="Script" preCondition="classicMode,runtimeVersionv4.0,bitness32" responseBufferLimit="0"/>
<add name="ExtensionlessUrlHandler-Integrated-4.0" path="*." verb="*" type="System.Web.Handlers.TransferRequestHandler" resourceType="Unspecified" requireAccess="Script" preCondition="integratedMode,runtimeVersionv4.0"/>
<add name="ExtensionlessUrlHandler-ISAPI-4.0_64bit" path="*." verb="*" modules="IsapiModule" scriptProcessor="C:\Windows\Microsoft.NET\Framework64\v4.0.30319\aspnet_isapi.dll" resourceType="Unspecified" requireAccess="Script" preCondition="classicMode,runtimeVersionv4.0,bitness64" responseBufferLimit="0"/>
<!--IISFIX: WebDAV is also buggy, and interferes with client requests-->
<remove name="WebDAV"/>
</handlers>
7.2.3. Settings panel not loaded¶
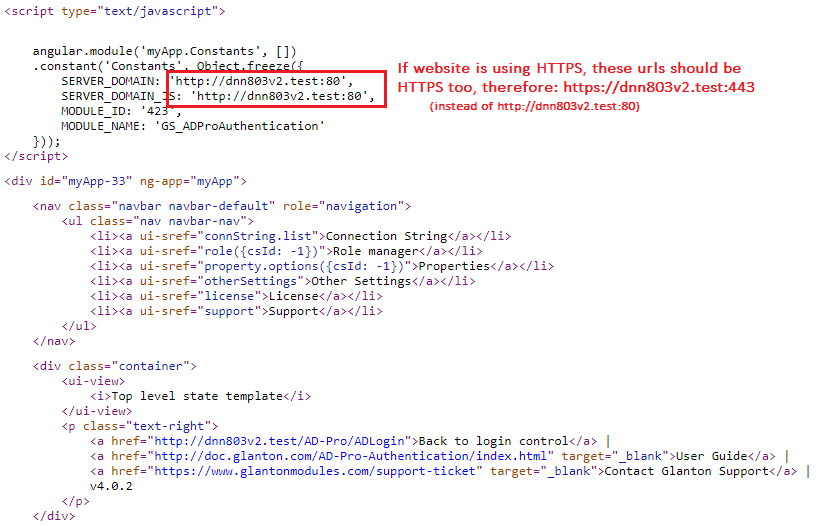
If website is working at the top of HTTPS protocol and it’s behind the load balancer there could be issue where the user interface is not displayed at all.
Usually it’s because JavaScript files reqired by the AD-Pro plugin are trying to be requested via HTTP protocol instead of HTTPS.
To confirm that please check the source code of the DNN page where the Glanton plugin is (click CTRL+U), and look for a string SERVER_DOMAIN or SERVER_DOMAIN_JS, see attached picture.
To correct this issue the DNN website needs to know that we are using HTTPS.
Sign in as DNN Administrator or Host.
Go to “Security” menu, see figure below.
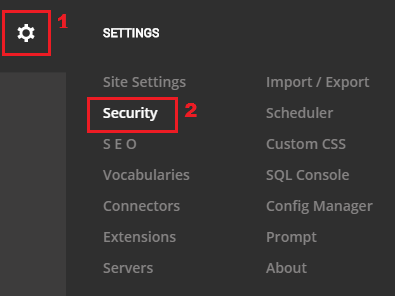
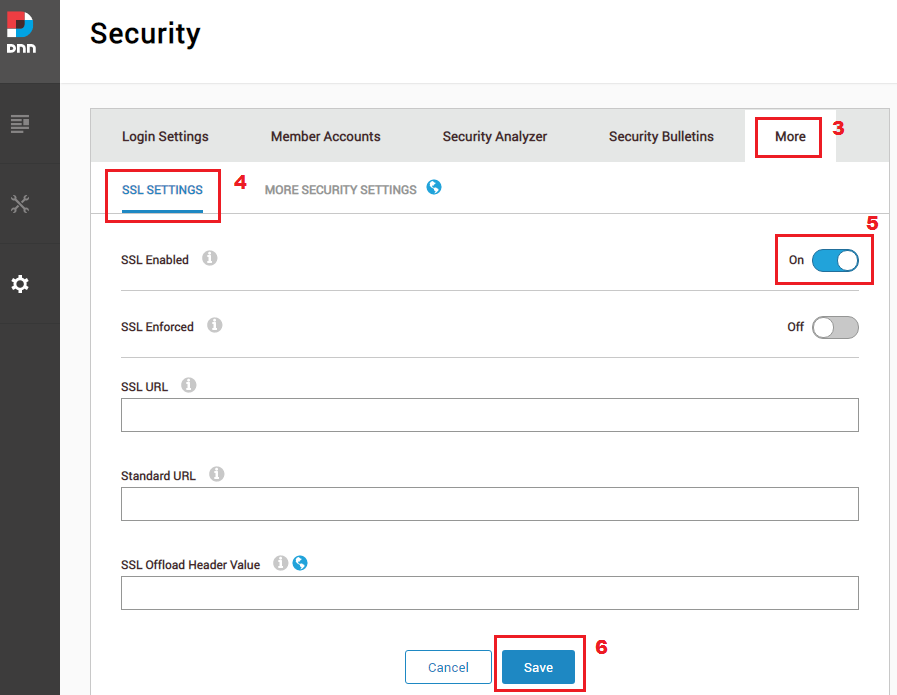
Click on tab “More” then “SSL SETTINGS”. Enable option “SSL Enabled” and save settings, see figure below.
To confirm check the page source once again.
7.2.4. View can’t be loaded¶
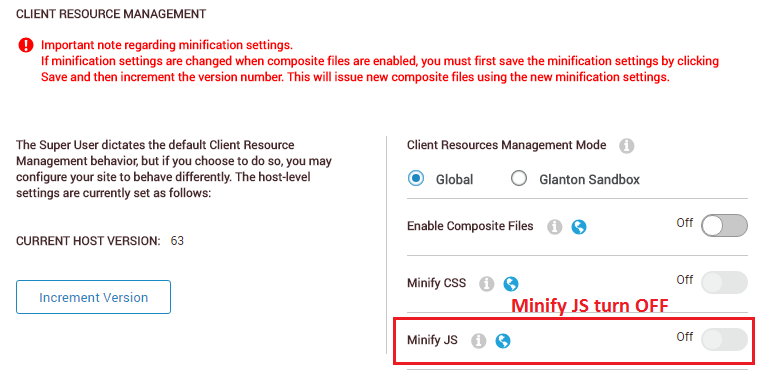
If you see situation like on figure below, where only upper part of interface is loaded and instead of bottom part of interface is displayed message Top level state template, probably it’s caused by minified js file.
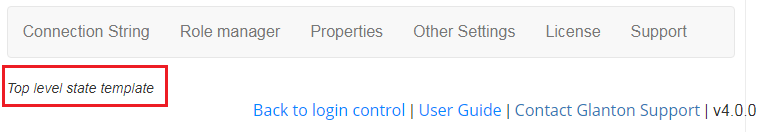
To fix that issue sign in as DNN host and go to menu “Servers-> Server Settings”.
At the bottom is section responsible for reducing Java Script files, please disable Minify JS attribute. See figure below for more info.
7.3. Signing Certificate - issues¶
Sometimes certificate thumbprint entered in “ADFS-Pro Authentication” is incorrect. To check that follow steps below:
- Ensure that you are logged on to the primary AD FS server.
- Open Windows PowerShell and run the following command:
Add-PSSnapin "microsoft.adfs.powershell" - You can alse check the current signing certificates using following command:
Get-ADFSCertificate –CertificateType token-signing - Look at the command output to see the Not After dates of any certificates listed.
- To generate (renew and update) a new certificate, execute the following command on the AD FS server:
Update-ADFSCertificate –CertificateType token-signing - To verify certificate run following command:
Get-ADFSCertificate –CertificateType token-signing - Two certificates should be listed now, one of which has a Not After date of approximately one year in the future and for which the IsPrimary value is False.
7.4. Certificate is not in the trusted people store¶
If you get following error message:
The X.509 certificate CN=*** is not in the trusted people store. The X.509 certificate CN=*** chain building failed. The certificate that was used has a trust chain that cannot be verified. Replace the certificate or change the certificateValidationMode. A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider.
Follow instructions from article Exporting Certificates to Client Machines
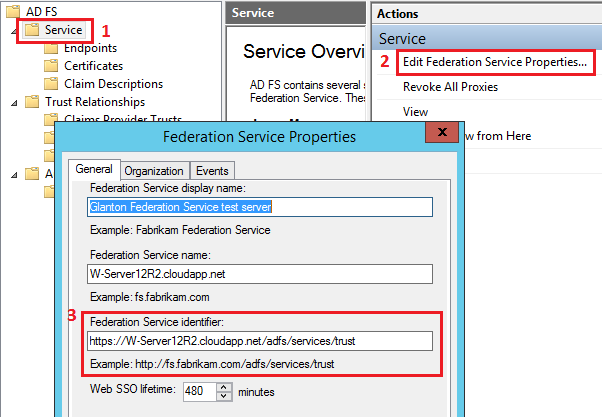
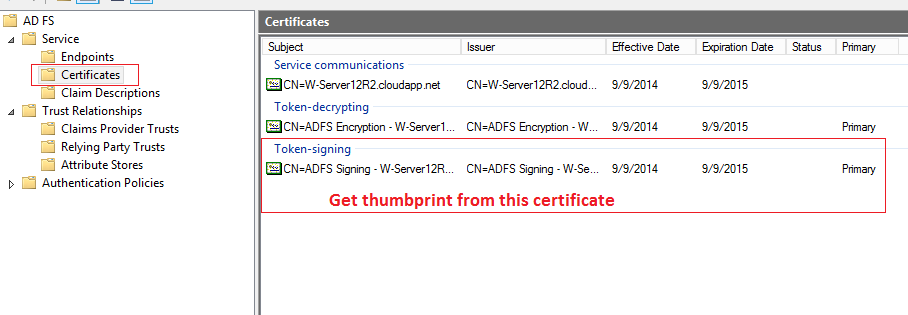
7.5. Key mapping for Security Token¶
If you get message like:
WIF10201:
No valid key mapping found for securityToken: "System.IdentityModel.Tokens.X509SecurityToken"
and issuer: "https://W-Server12R2.cloudapp.net/adfs/services/trust"
Please make sure that:
in “ADFS-Pro Authentication” attributes: “Issuer Name Registry” and “Valid Issuers” are equal to Federation Service Identifier in ADFS,
certificate thumbprint is valid,
7.6. The Audience Restriction Condition was not valid¶
If you get the message like:
ID1038:
The AudienceRestrictionCondition was not valid because the specified Audience is not present in AudienceUris.
Audience: 'https://MyDnn.cloudapp.net/'
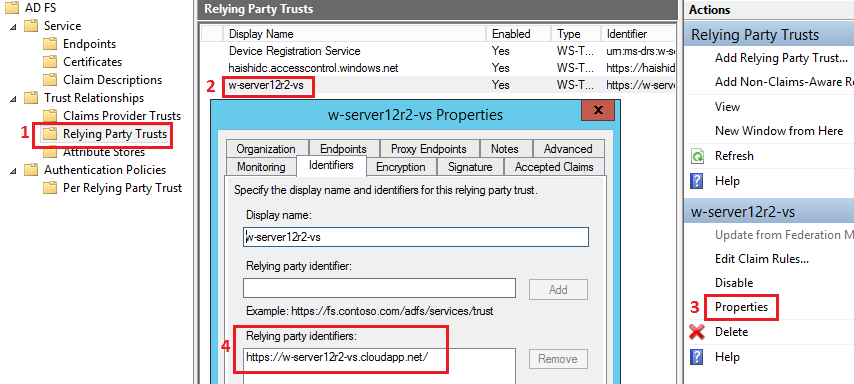
Please make sure that following values are equal:
Audience Uris - in WS Provider,
Realm - in WS Provider,
Relying Party Identifier - in ADFS (screen below);
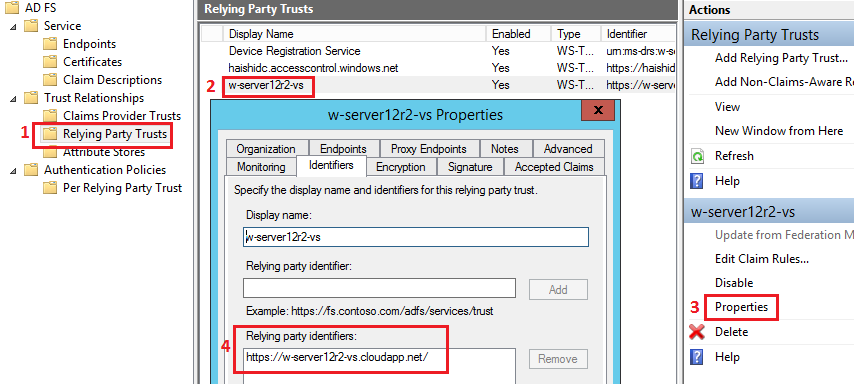
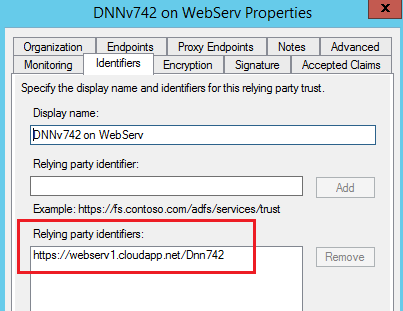
7.7. Relying party trust is unspecified¶
If in Event Viewer on ADFS server, you get message like:
Microsoft.IdentityServer.Web.InvalidScopeException: MSIS7007:
The requested relying party trust 'https://w-server12r2-vs.cloudapp.net/' is unspecified or unsupported.
If a relying party trust was specified, it is possible that you do not have permission to access the trust relying party.
Contact your administrator for details.
Please make sure that “Realm” specified in DNN in “ADFS-Pro Authentication” provider is equal to “Relying Party Identifier” in ADFS (screen below).
7.8. URL scheme is not https¶
If you get the message like:
ID1059:
Cannot authenticate the user because the URL scheme is not https and requireSsl is set to true in the configuration,
therefore the authentication cookie will not be sent.
Change the URL scheme to https or set requireSsl to false on the cookieHandler element in configuration.
Please make sure that the DNN is using https, or set require SSL attribute to false.
Open the web.config file and set <cookieHandler requireSsl="false" />.
7.9. Issuer was not recognized by the IssuerNameRegistry¶
If you get the message like:
ID4175:
The issuer of the security token was not recognized by the IssuerNameRegistry.
To accept security tokens from this issuer, configure the IssuerNameRegistry to return a valid name for this issuer.
Please make sure that the following attributes are correct:
- certificate thumbprint,
- Issuer Name Registry,
7.10. Could not load the identity configuration¶
If you get the message like:
ID7027:
Could not load the identity configuration because
no <system.identityModel> configuration section was found.
Please make sure that web.config file has these lines:
<section name="system.identityModel" type="System.IdentityModel.Configuration.SystemIdentityModelSection, System.IdentityModel, Version=4.0.0.0, Culture=neutral, PublicKeyToken=B77A5C561934E089" />
<section name="system.identityModel.services" type="System.IdentityModel.Services.Configuration.SystemIdentityModelServicesSection, System.IdentityModel.Services, Version=4.0.0.0, Culture=neutral, PublicKeyToken=B77A5C561934E089" />
7.11. STS address is not configured¶
If you get the message like:
ID1058:
A valid STS address is not configured on the WSFederationAuthenticationModule for creating WS-Federation passive protocol SignOut requests.
Set the Issuer property on the module to a valid STS address.
Please make sure that are equal:
Realm field in the “ADFS-Authentication” module .
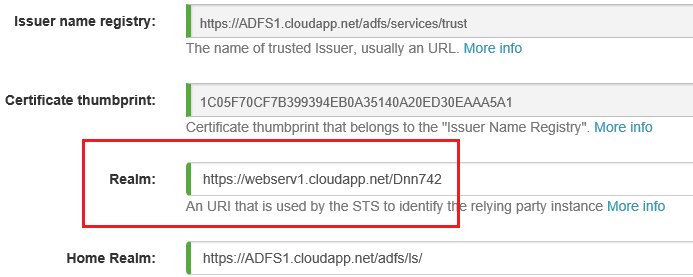
“Relying party identifier” in the ADFs config.
7.12. SignInResponse issue¶
If you get message like:
ID3206:
A SignInResponse message may only redirect
within the current web application: ‘https://MyDnn.cloudapp.net’ is not allowed.
A return url address must have / at the end.
In the logs should be info about your current url.
7.13. Handlers on path /adfs/ls/¶
If in AD Event Viewer you get the message like:
Microsoft.IdentityServer.RequestFailedException:
MSIS7065:
There are no registered protocol handlers
on path /adfs/ls/ to process the incoming request.
atMicrosoft.IdentityServer.Web.PassiveProtocolListener.OnGetContext(WrappedHttpListenerContext context)
To fix that issue:
- ensure that SPNs are correct,
- ensure that the certificate is not expired,
7.14. Unobtrusive Validation Mode¶
If you get the exception like:
System.InvalidOperationException:
WebForms UnobtrusiveValidationMode requires a ScriptResourceMapping for ‘jquery’.
Please add a ScriptResourceMapping named jquery(case-sensitive).
To fix that issue make sure that in web.config file under appSettings section is following entry:
<appSettings>
...
<add key="ValidationSettings:UnobtrusiveValidationMode" value="None" />
...
</appSettings>
If this key value is set to None [default], the ASP.NET application will use the pre-4.5 behavior
(JavaScript inline in the pages) for client-side validation logic.
For more info see ASP.NET appSettings Element
7.15. Cryptographic exception - cookie encrypt¶
If you get the message like:
ID1074:
A CryptographicException occurred when attempting to encrypt the cookie
using the ProtectedData API (see inner exception for details).
If you are using IIS 7.5, this could be due to the loadUserProfile setting
on the Application Pool being set to false.The data protection operation was unsuccessful.
This may have been caused by not having the user profile loaded for the current thread’s user context,
which may be the case when the thread is impersonating.
Please make sure that the following code is in your web.config file:
<system.identityModel>
<identityConfiguration>
<securityTokenHandlers>
<remove type="System.IdentityModel.Tokens.SessionSecurityTokenHandler, System.IdentityModel, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089" />
<add type="System.IdentityModel.Services.Tokens.MachineKeySessionSecurityTokenHandler,
System.IdentityModel.Services, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089" />
</securityTokenHandlers>
</identityConfiguration>
</system.identityModel>
More info can be found in article Running WIF Based Apps in Windows Azure Web Sites
If DNN is hosted on a web farm or behind the loadbalancer read Session token encryption chapter.
Make sure that IIS AppPool has enabled attribute
Load User Profile, see figure below: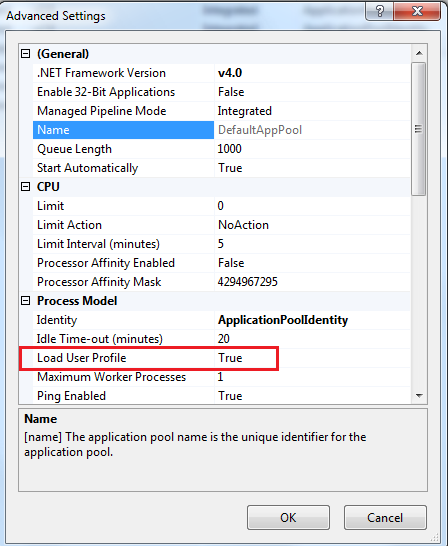
7.16. Cryptographic exception - cookie decrypt¶
If you get an error message like:
System.InvalidOperationException ID1073:
A CryptographicException occurred when attempting to decrypt the cookie
using the ProtectedData API (see inner exception for details).
If you are using IIS 7.5, this could be due to the loadUserProfile setting
on the Application Pool being set to false.
This could happen when DNN is hosted on the server that is behind the load balancer. In this case server is deployed on multiple machines for example on a web farm. When user continue to browse the site (after login) the load balancer redirects some request to execute on machine-1 some on machine-2. If machine-1 receives the first request after login then WIF uses machine-1’s current user key to encrypt the cookie. When the next request goes to machine-2, WIF in machine-2 will fail to decrypt the cookie using machine-2’s current user key and you will get the error like above.
To fix that issue a certificate need to be used to decrypt/encrypt the session tokens.
Add following entry in web.config file to use certificate:
<configuration>
<system.identityModel.services>
<federationConfiguration>
<serviceCertificate>
<certificateReference x509FindType="FindByThumbprint" findValue="<cerrt-thumbnail>"
storeLocation="LocalMachine" storeName="My"/>
</serviceCertificate>
</federationConfiguration>
</system.identityModel.services>
</configuration>
See this article for reference.
7.17. System.Web.HttpException (0x80004005)¶
If the DNN
System.Web.HttpException (0x80004005): Server cannot set status after HTTP headers have been sent
7.18. Too many browser sessions¶
By default DNN redirects to AD FS login page, then after entering credentials, it should redirects user back to website. But if instead of that login process stuck in loops and following error message is displayed:
MSIS7042:
The same client browser session has made '6' requests in the last '1' seconds.
Contact your administrator for details.
The solution is to reduce the number of claims that are issued to the DNN to the bare minimum fields, like: Unique Claim and Identity Claim.
This issue is related to the Chrome browser that has changed the security model for how it handles ADFS logins.